Security implementations & practices
Contents
Security implementations & practices#
This page delves into the implementation and practices of OpenSPP, highlighting its adherence to the principles of zero-trust architecture, user authentication, input/output validation, session management, cryptographic management, file management, and robust logging.
OpenSPP has been designed around the zero-trust architecture principle. This principle involves the fundamental premise of not automatically trusting anything inside or outside its perimeters. Instead, it verifies everything trying to connect to its systems before granting access. This approach fortifies OpenSPP's security framework, protecting it from both internal and external threats.
The solution accommodates multiple authentication systems, allowing for integration with external ID systems such as Keycloak or MOSIP. Moreover, OpenSPP clearly articulates each functionality’s scope and role capabilities, effectively decoupling them from the main business logic, instead promoting system clarity and integrity.
OpenSPP promotes tools for monitoring user behavior, devices, and services. It supports log analysis and event monitoring, enabling proactive identification and response to potential security incidents. This level of surveillance enhances the platform's overall security, providing real-time insights into system activities.
In OpenSPP, data inputs are strongly typed, sanitized, and parameterized, ensuring input validation. This process prevents malicious data from entering the system, thereby guarding against potential vulnerabilities. Additionally, the solution sanitizes and encodes all outputs, including error messages, to prevent unintended disclosure of confidential or internal information.
OpenSPP ensures secure session management by utilizing well-vetted algorithms that generate random session identifiers. These algorithms create new session identifiers upon re-authentication and terminate session identifiers post-logout, reinforcing the overall security framework.
It uses cryptographic algorithms vetted for encryption/hashing during data transit or at rest. The encryption keys are generated, protected, and stored securely. Depending on a country's requirements during implementation, a Hardware Security Module (HSM) or SoftHSM can be deployed for added cryptographic security.
As for file management, OpenSPP whitelists file formats and limits file sizes for uploaded documents, ensuring system efficiency and security. Additionally, OpenSPP is designed not to store confidential data while logging, safeguarding sensitive information from potential exposure.
OpenSPP has a configurable logging mechanism covering all assets, with selectable log levels per configurations. This robust logging mechanism is integral to the platform's security strategy, offering valuable insights into system activities.
OpenSPP is committed to maintaining its security posture by conducting regular vulnerability assessments and penetration testing (VAPT) of its applications, APIs, and infrastructure. Security assessments are carried out during the development stage and post-deployment, ensuring that the platform consistently adheres to the highest security standards.
Privacy#
The following section elaborates on OpenSPP's consent management framework and its emphasis on data privacy principles.
A comprehensive consent management framework lies at the core of OpenSPP’s user-centric approach. This built-in mechanism ensures that user consent is sought, stored, and managed appropriately. By actively incorporating user consent into its operations, OpenSPP ensures that users retain control over their data, fostering trust and transparency.
OpenSPP promotes the conduct of regular privacy risk assessments. These assessments identify potential privacy risks and provide insights into how to mitigate them. Regular assessments not only uphold the integrity of the system but also instill confidence among users regarding safeguarding their data.
OpenSPP adheres to the principles of data minimization, where it is designed to collect only the minimum amount of data necessary to fulfill a given task. This principle is integral to OpenSPP's data handling policy and ensures that unnecessary or excessive data is not collected or retained. This strategy reduces the potential exposure of user data, thereby enhancing the privacy protection OpenSPP offers.
Recognizing the importance of the right to be forgotten, OpenSPP has mechanisms to cater to requests for data deletion or anonymization. This feature empowers users to control their data post-submission and significantly reinforces user trust in the system.
Data#
One of the core facets of OpenSPP's design is its robust approach toward data management and security. This section provides a detailed exploration of how OpenSPP handles various aspects of data, emphasizing its commitment to integrity, security, and efficiency.
Data anonymization is a fundamental principle that OpenSPP aligns with, taking substantial measures to protect sensitive and identifiable data. The solution incorporates various principles such as minimizing identifiability, protecting sensitive data, ensuring data security, and implementing constant data monitoring. However, OpenSPP acknowledges that there's a need for more extensive implementation of data anonymization principles. Strategies, including data masking and randomization, are planned for future deployment, fortifying OpenSPP's commitment to preserving data privacy.
At the architectural level, OpenSPP's logical data architecture facilitates layers of separation across various data types, including transactional, workflow, operational, audit, analytical, and Master Data Management (MDM) data. This segregation is accomplished by distributing data across multiple tables per specific business requirements, allowing for enhanced data management and improved system performance.
OpenSPP is built with a strong emphasis on data security and integrity. The solution supports encryption for data both at rest and in motion, which prevents unauthorized access and ensures data confidentiality. Measures such as strong authentication, access control, data backup, and recovery plans, along with regular monitoring and auditing of data, are implemented to guarantee data integrity. OpenSPP plans to implement additional data integrity checks like checksums, hashes, and digital signatures, further enhancing the security framework.
Security for data-in-motion is achieved through support for Transport Layer Security (TLS) via encryption, authentication, and access control. The solution can also support advanced protective measures like intrusion detection systems (IDS) and network segmentation based on the specific deployment requirements of the country.
The solution is designed to handle varying data demands, including scenarios of low latency-high volume and vice versa. This flexibility ensures optimal system performance regardless of the use case or business/implementation requirements, enabling OpenSPP to cater to various scenarios.
Security architecture#
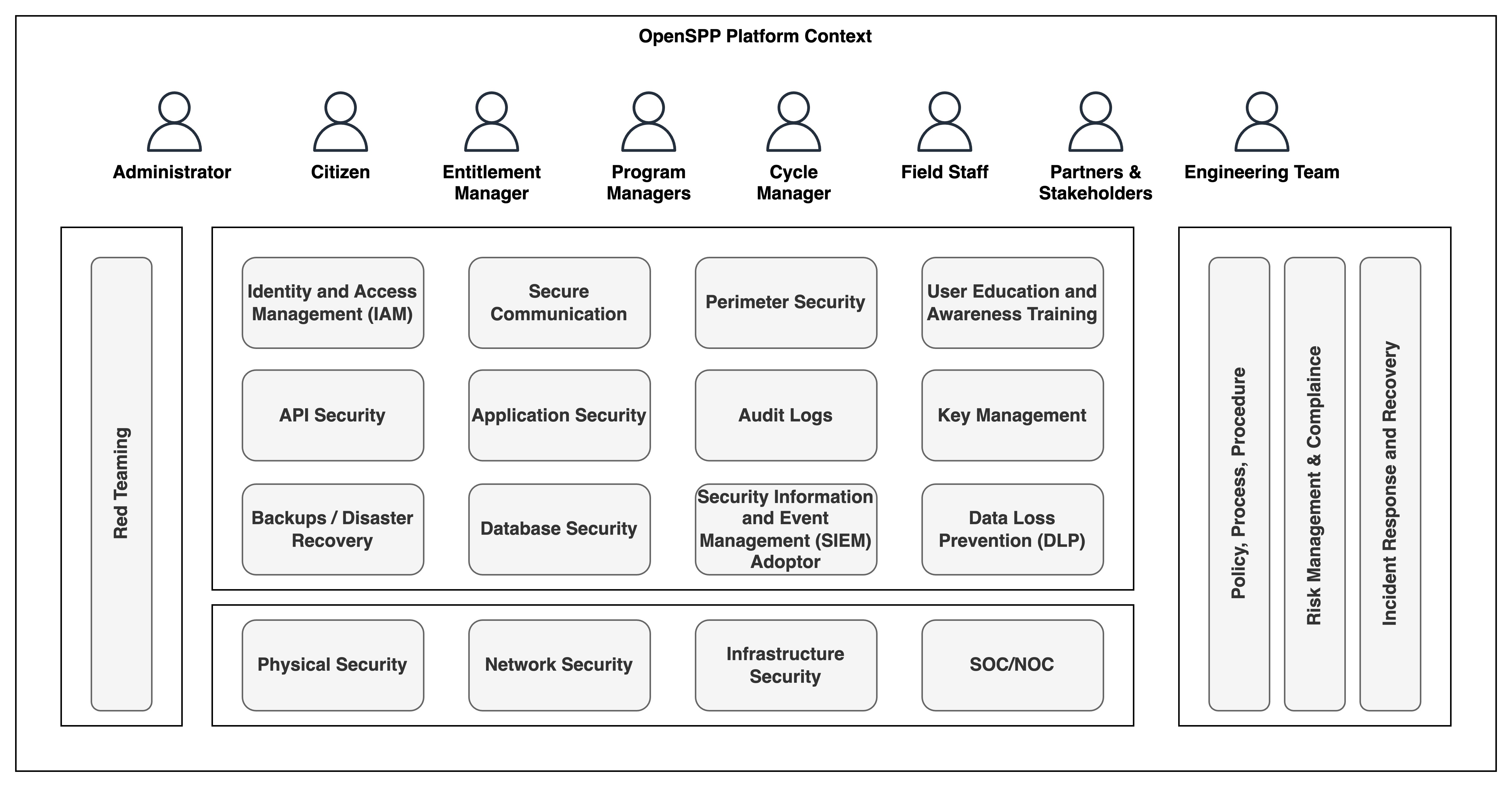
The OpenSPP platform can operate in a cloud environment as well as an on-prem environment while ensuring security and management across several key security domains, as listed below,
Identity and Access Management (IAM): This involves managing user identities and controlling access to resources within the platform to prevent unauthorized access.
API Security: This domain focuses on securing APIs to ensure that interaction between different software applications remains secure.
Backups/Disaster Recovery: This area is dedicated to securing data by creating backups and planning for quick recovery in case of a disaster.
Physical Security: Measures are in place to protect the platform’s physical assets, including hardware and facilities.
Secure Communication: The platform enforces secure communication protocols to protect data in transit.
Application Security: This pertains to measures and protocols that are designed to protect the platform's applications from threats and vulnerabilities.
Database Security: Ensures the protection of databases against compromises of their integrity, confidentiality, and availability.
Network Security: Involves protecting the integrity and usability of network and data, both on-site and off-site.
Perimeter Security: A defense mechanism for the outermost boundaries of the platform to detect and prevent attacks.
Audit Logs: Keeping detailed logs to track user activities that can be reviewed during security audits.
Security Information and Event Management (SIEM) Adaptor: This adoptor feeds data into the SIEM.
Infrastructure Security: Measures to protect the platform’s infrastructure, including systems, networks, and data centers.
SOC/NOC: Continuous observation of the platform's systems and networks to quickly identify and address potential security issues.
User Education and Awareness Training: Equipping users with the knowledge and skills to protect the platform and its data.
Key Management: Handling cryptographic keys within a cryptosystem, including their generation, exchange, storage, use, destruction, and replacement.
Data Loss Prevention (DLP): Strategies to prevent sensitive data from being accessed, used, or disclosed by unauthorized users.
Policy/Process Procedure: Establishing and maintaining policies and procedures that govern the operation and use of the platform.
Risk Management and Compliance: Identifying, assessing, and controlling threats to the platform's operations.
Incident Response and Recovery: A dedicated framework for addressing security breaches effectively, ensuring swift action and restoration of normal operations following an incident.
Red Teaming: This critical security practice involves challenging the platform’s defenses by simulating sophisticated cyber-attacks, ensuring vulnerabilities are identified and mitigated proactively.
Each domain is interconnected and plays a crucial role in maintaining the integrity and resilience of the OpenSPP platform. At the foundational layer, these security domains are influenced by the specific country's context. The implementation of security measures varies, with some being fully realized and others partially, all driven by the unique requirements of each country.
 openspp.org
openspp.org